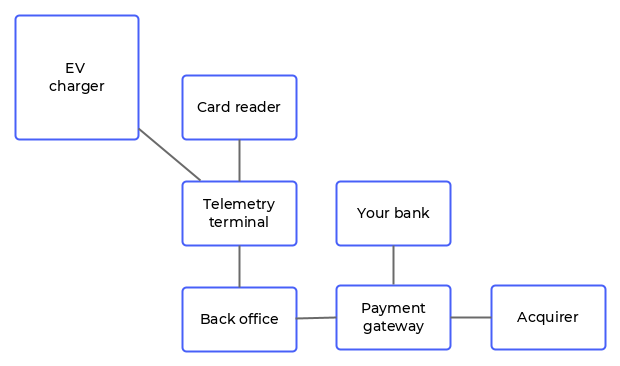
The payment terminals consist of a compact contactless reader and a telemetry unit. This two-part design allows you to position modules more conveniently inside the charger enclosure and reduces costs if replacements are ever needed. The terminals require a 12V power source and connect to the EV charger via a standard Ethernet connection.
Message exchange between terminal and charger is carried out over MQTT. Several transaction types are supported, such as a flat rate or a card pre-authorisation to begin charging with a final confirmation when charging ends. Multiple chargers or charging handles can make use of a single payment terminal, as the messaging protocol allows for transactions to be matched to individual charging sessions.
All sensitive card data remains secure at all times as it is encrypted in the reader and transmitted over a secure channel to the acquiring bank. The reader’s security is certified to PCI PTS 5.1.
Bank cards, smartphones and wearables are all accepted. This includes devices featuring Visa, Mastercard, GooglePay or ApplePay. The payment terminal can handle non-payment cards and tags as well, so loyalty and membership schemes can all use the same contactless reader.
Transaction processing and reporting are done by our partner, payment gateway Switchio. Funds are cleared by Elavon, the leading acquirer offering fast and reliable customer experience with next day fund transfer options.